The focus of any deception technology is to stop a cyber criminal from accessing a network and doing any substantial harm. The honeypot technique technology works by creating ploys or deception traps that mimic certain system assets throughout the structure. These decoys can produce computer-generated or real operating system settings.
A honeypot technique technology is a trick that is laid down by an IT professional for malicious cyber criminals; they anticipate that they will use it for interaction and thus leave useful information for intelligence. Honeypot is among the earliest techniques of IT, but tricking cyber criminals into a network can be disastrous but according to Norton is the best starting place.
You can also read: What are the two readings on a pulse oximeter
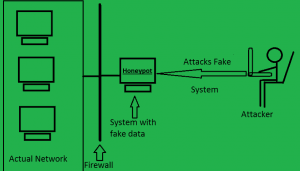
How Honeypot Works – Illustrated With a Diagram
 Honeypots are strategically built to hoax the cyber criminal into believing they have found a way to alter rights and steal authorizations.
Honeypots are strategically built to hoax the cyber criminal into believing they have found a way to alter rights and steal authorizations.
When the trap is triggered, an alarm is sent to a central deception server that takes note of the affected decoy and the attack vectors that were used by the cyber criminal.
It is designed deliberately with known exposures in the area to lure or obvious target for invaders.
A honeypot can’t comprise production data or take part in genuine traffic of a network. This indicates that how you will find out anything taking place within it is an outcome of an attack. If someone’s stopping by, they’re up to no good.
The Origin of the HoneyPot Technique
The earliest honeypot emerged in 1989 and was conducted by Clifford Stoll during his earlier work at Lawrence Berkeley Laboratory 2. The new honeypots were mainly used for the investigation to scrutinize attacks on a network and were resource-intensive to run, sustain, and examine. It was advanced in 1999 when Lance Spitzner implemented the Honeynet Project 3, which has continued to grow in the research organization.
 Later, Niels Provos implemented honeyd4 in an attempt to make an easily installed virtual honeypot. This device delivered rivaled virtual hosts on a network that were fashioned to sense the presence of a malicious cyber criminal.
Later, Niels Provos implemented honeyd4 in an attempt to make an easily installed virtual honeypot. This device delivered rivaled virtual hosts on a network that were fashioned to sense the presence of a malicious cyber criminal.
Usually, a body positioned a honeypot on the border outdoor of a production network, and it would wait for incoming network interference to engage with the decoy. The building of honeypots positioned superior emphasis on gathering over-all research and danger actor intelligence than it did on satisfying the role of in-network threat recognition. This means that there are pros and cons of honeypots to all organizations such as TechPiton.
Pros of Honeypots
The introduction of deception technology for cyber defense has added valuable assets that are changing the asymmetry of cyber-attack. Organizations place deceptive decoys, breadcrumbs, and lures throughout the network to make the entire environment a trap.
 This turns the whole environment into a virtual minefield to proactively lure and misdirect an in-network attacker into engaging and revealing their presence.
This turns the whole environment into a virtual minefield to proactively lure and misdirect an in-network attacker into engaging and revealing their presence.
Making the entire network a trap, information security teams can go on the defense side against attackers, allowing them to detect an attack early in the cycle, gather company-specific threat intelligence, and derail the attacker before they can do any severe damage.
Deception platforms are also instrumental in attack analysis, forensics, and remediation. Deception systems automate the correlation of attack data and raise only substantiated alerts that are backed by details on the attacker’s tactics.
It provides an advanced platform where the security teams can also gain the ability to slow down an attack in progress by redirecting the threat actor away from a production system to a decoy, while leading an attacker to believe they have successfully escalated their attack.
This capability provides the security team with substantiated alerts and the threat intelligence required to capture and classify attack-related movement, including indicators of compromise from the attack. This company-specific information simplifies attack analysis, forensic reporting, and enables automated incident response actions such as blocking, quarantine, and threat hunting.
You may also read: Best website designers in Kenya
Cons of Honeypots
Modern cyber criminals are more erudite, violent, and have they have more substantial resources than before. The system is no longer adequate to keep attackers out.
Even with the more advanced security controls measures; errors and misconfigurations often occur. Additionally new types of attacks occur on the network, and no security resolution can be considered to be 100% effective in dealing with these attacks.
 Organizations that are overly dependent on prevention technologies will inevitably have a detection gap, where an attacker could successfully breach the perimeter and move undetected through the environment for months.
Organizations that are overly dependent on prevention technologies will inevitably have a detection gap, where an attacker could successfully breach the perimeter and move undetected through the environment for months.
However, relying on a honey pot to detect these attackers, post-breach is limited by the inherent shortcomings of an emulated virtual host and the logistics of deploying a conventional honeypot.
The other limitation of the honeypot technique is that modern cyber criminals can often recognize emulated honeypot systems. They then thumbprint them and evade interacting with them. This makes it hard to authenticate the order.
There is also the con in terms positioning, Honeypots don’t have a centralized deployment system and usually need one per network sector. Reorganizing honeypots requires as much determination as to their primary connection.
Deception Techniques For Visibility, Early Detection, And Risk Mitigation
Most people have used deception techniques in pursuing, gaming, law execution, and military domains, including playing a crucial part in the most massive military operation in history.
Summary
Deception technology has advanced theatrically from the original idea of honeypots and evolved into a comprehensive security platform that is easy to deploy and manage. Modern deception plays a vital role in correctly sensing, and proficiently reacting to, in-network dangers irrespective of the attack route or attack surface.
Additionally, integrating deception technology with other components of the security stack improves automation and can dramatically improve incident response efficiency and effectiveness.
New deception platforms can extend onto the endpoints, where attackers frequently leverage stolen credentials or mis configurations to expand their foothold across the environment. By inserting deceptive credentials into the host, or even intercepting an attacker’s efforts to leverage network authentication systems such as Active Directory, the information security team gains valuable insights and visibility in an attacker’s activities while making the task much more complicated for a malicious actor.
Selecting the best deception solution for a given organization distills down to meeting an organization’s needs for operational efficiency, versatility, range of deception, authenticity, and effectiveness.

